So there you are, staring at a folder full of mystery files. some are labeled, some are encrypted, some are just… suspicious. you could open each one manually like it’s 2005, or you could do what any self-respecting IT wizard would do: fire up powershell and unleash the full wrath of azure information protection ( AIP ).
Because when it comes to knowing who’s been naughty with sensitive data, aip doesn’t just hand you the receipts. it hands you a scriptable audit trail.
Let’s get nerdy
First, make sure you’ve got the right aip client.
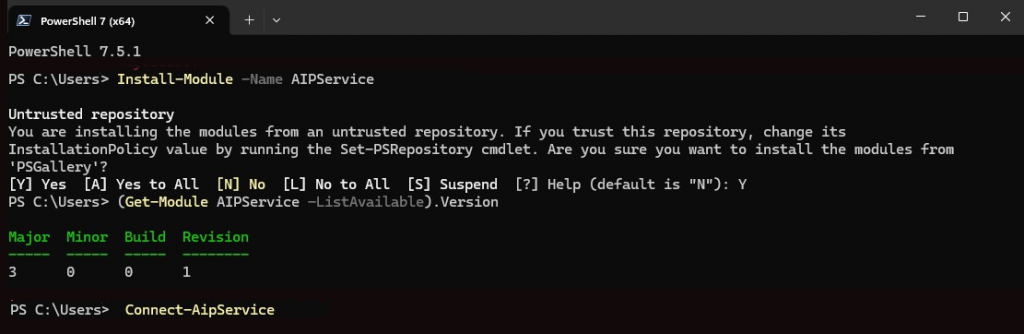
Install-Module -Name AIPService
(Get-Module AIPService –ListAvailable).Version
Connect-AipServiceif powershell doesn’t cough up a version, congrats … you’re already in trouble. go install the client and try again.
Become the chosen one: enable super user mode
Before you start poking around protected files , you need the proper clearance.
Enter: AIP super user mode.
Without it, you’re just a regular mortal trying to lift thor’s hammer. super user status lets you inspect, decrypt, and re-label files even if you weren’t the original owner. to activate this mode, you’ll need admin creds and a little powershell spell:
Add-AipServiceSuperUser
-EmailAddress <YOUR EMAIL ADRESS>Pro tip: your account must be on the list of authorized super users in the aip portal. Otherwise, you’ll get stonewalled faster than someone trying to access HR’s budget folder during bonus season.
Finally ! Meet your new best friend: get-aipfilestatus
This cmdlet is basically a lie detector for files. you throw it a path, and it tells you if a file’s labeled, protected, or just sitting around naked and afraid.
Get-aipfilestatus -path "c:\secretstash"
Applying labels like a boss
now that you’ve audited the chaos, it’s time to bring order. you’re going to use set-aipfilelabel. but fair warning—it doesn’t accept label names, only label IDs. because obviously, why make life easy. So you go grab the label ID from the aip portal, and then fire :
Set-aipfilelabel -path "c:\secretstash\projectx.docx" -labelid <LABEL ID>
Boom! Labeled! Classified! Safe! Your ciso would be proud!
Automatic classification? Yes, please
Feeling lazy or just love automation? Let The AIP scanner youfiles stored on-premises (think: file shares, legacy folders, digital tombs)? and slap on the right label based on built-in rules. it’s like a compliance intern that doesn’t need coffee or emotional support.
The aip scanner is a background service you install on a windows server. you configure it to crawl specific locations, analyze files against your label policies, and apply the right labels based on content.
great for:
- old data you want to clean up
- shared drives that haven’t been touched since 2012
- bulk-classifying terabytes of stuff without user interaction
the scanner uses the same sensitivity labels and rules from your tenant, so everything stays consistent.
Sit back and let the robots sort your secrets.
What about encrypted files from another org?
Ah ….now we hit the brick wall.
So your file is locked tighter than a vault, and you’ve got no idea why powershell is giving you the cold shoulder. Turns out the encryption came from another tenant … let’s say, contoso.com ( how suspicious ) … and your tenant has exactly zero rights to touch it. Zero !
Even with super user mode, powershell just shrugs and says:

Translation: nope ! Not today satan !
If you’re lucky, you can reach out to the person who uploaded the file, maybe they’re on the allowed users list. Ask them to open it, copy the contents, and dump it into a clean, label-free file. old-school, but it works.
The bottom line
AIP and Powershell together are like a swiss army knife with a laser beam. You can scan, label, protect, report, and fix misclassified files at scale. or you can watch users mislabel payroll data as “general” and pretend everything’s fine.
Your call.
If you’re tired of babysitting labels through the gui and want to wield some real admin power, open powershell and let the classification games begin. just remember … when encryption is from another tenant, you’re not a hacker. you’re just a guest with no keys.
Got questions? Want scripts? Or just want to vent about users labeling their cat photos as “confidential”? I’m here for that too.











